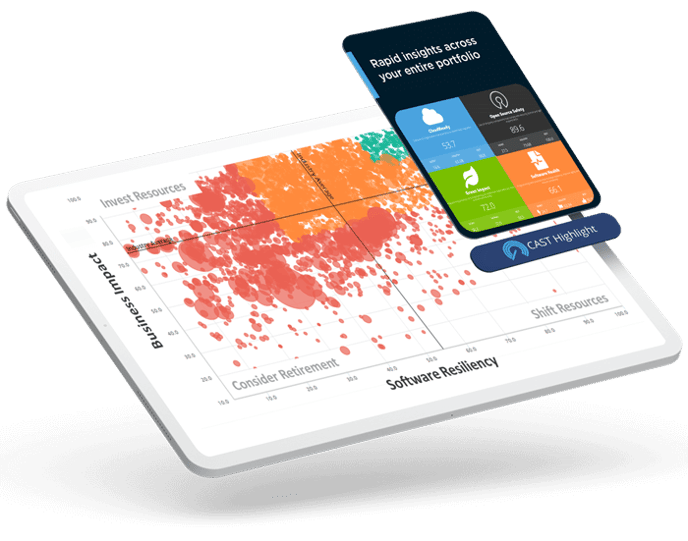
CAST Highlight
The control tower for your custom application portfolio
Automated observability and governance for your custom-built software.
Instant insights across hundreds of applications. Operational in a week.
Trusted by
Hard facts to steer and
report on strategic imperatives
Cloud | Technical Debt | Compliance | Costs | Sustainability
Software intelligence at your fingertips
cloud maturity, technical debt, software composition, resiliency, agility, maintenance costs, green impact
- What are my best opportunities to reduce costs?
- Do I have new legal and IP exposures this month?
- Are risky components, like Log4J, still being used?
- Who exactly is using the custom framework we built?
- Are we making progress in getting ready for cloud?
- Are we optimizing for cloud the software already there?
- What needs to change? How much work is involved?
- Which projects are more likely to be derailed?
- Are critical systems likely to go down in production?
- How do I make my software greener and show that?
- What do I keep improving, in a most efficient way?
CAST Highlight enables
Ongoing reduction of maintenance costs and technical debt
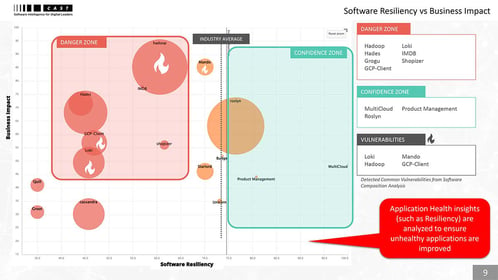
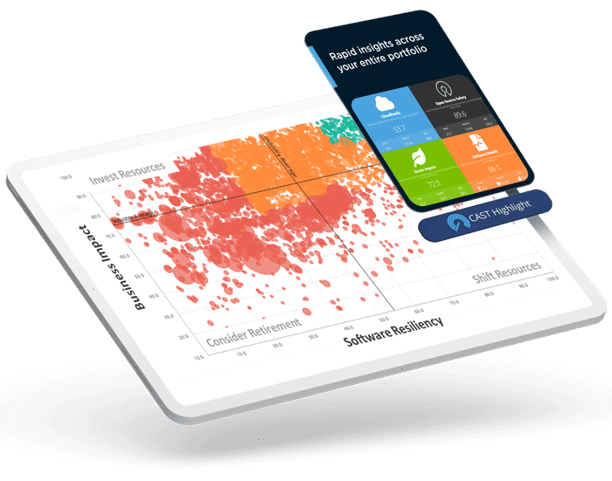
Leaders have a single, integrated view of their portfolio. Based on facts and auto-recommendations, they can see where to lower maintenance costs, optimize resource allocation, reduce technical debt, rationalize redundancies, and avoid production outages.

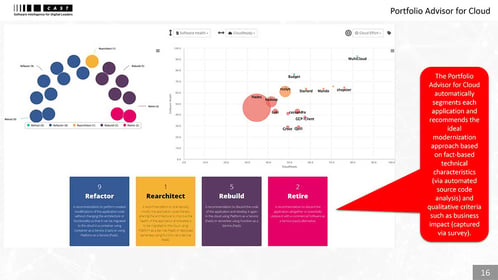
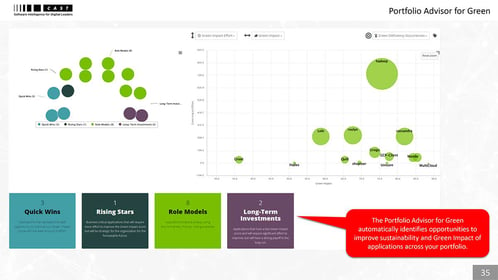
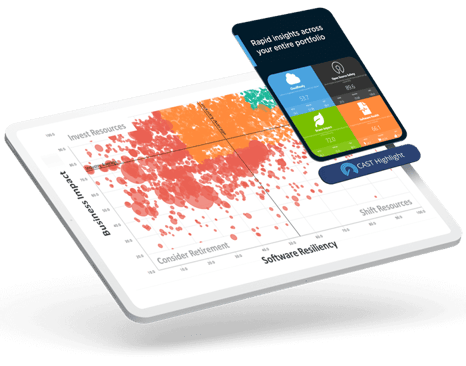
Faster cloud migration and ongoing optimization
Cloud leaders automatically segment and prioritize applications for migration (5Rs) and optimization in cloud based on technical characteristics and business impact. They can instantly drill down to see what needs to change in the code and how, the estimated effort, and best-fit cloud native services.

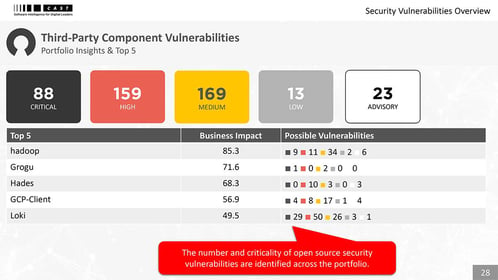
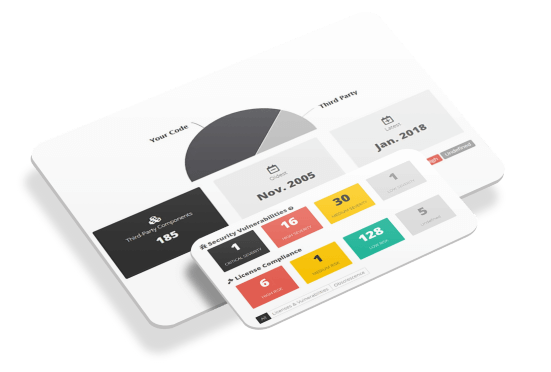
Stronger control of open-source legal and security risks
Traditional SCA technology can be costly, hard to manage, and fatiguing to developers. CAST Highlight is operational in weeks across all applications. Security, architecture, and compliance teams get automatic recommendations on priority actions helping them focus on the most critical security vulnerabilities and IP licensing exposures. Without disrupting developers.
Greener
software
Green software development is emerging as the next logical step for enterprises to make their technology more sustainable and meet emerging requirements. CAST Highlight pinpoints green deficiencies in the code and how to address them to lower CO2 emissions, while improving costs, performance, and resiliency.

Key Capabilities
AI-Powered · 50+ technologies · Customizable dashboards · Instant drilldowns · REST APIs · CI/CD plug-ins




Software health
- Resiliency, agility, technical debt insights
- Maintenance cost optimization advice
- Portfolio rationalization recommendations
- Trends and progress monitoring
- Benchmarking against industry peers
Cloud maturity
- Automated 5Rs recommendations
- Cloud native blocker insights
- Effort estimates & remediation advice
- Cloud native service recommendations
- Multi-cloud & container readiness insights
Software composition
- OSS licensing and IP risk identification
- OSS security vulnerability detection
- SBOM creation and importing
- Priority action recommendations
- Proprietary component governance
- Emerging vulnerability detection (weaknesses)
Green impact
- Quick win recommendations
- Green deficiencies identification
- Remediation advice and effort estimates
- Trends and progress monitoring
- Benchmarking against industry peers
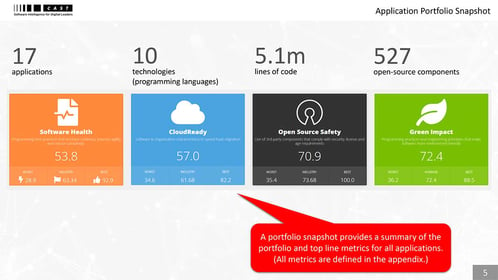
Sample Portfolio
Governance Report
See a sample portfolio report for 17 applications generated automatically by CAST Highlight – the application control tower.
What our clients experienced
We were able to get the product up and running in no time.
Tim Dufrane
IT Operations Manager
Norsk Titanium
Application cloud readiness assessments went from 3+ weeks down to 3 days with the same accuracy.
Jeremy Woo-Sam
Azure Blackbelts Lead
Microsoft
CAST accelerates the assessment & analysis phases of app modernization by up to 30X.
Sunil Agrawal
Chief Architect
LTI
CAST Highlight accelerates your Cloud Migration Project
Secure code analysis- only encrypted analysis results upload to the
SaaS
product.
Effortless Code scan provides Cloud Blocker/Booster, PaaS recommendations,
Resiliency and
CVVE scores.

Manish S.
Principal Software Engineer
Enterprise(> 1000 emp.)
CAST Highlight Reviews & Product Details
SaaS implementation means ready for Cloud, code scanning for OSS vulnerabilities and IP checks, works seamlessly with most languages and provides deep insights like blockers, effort estimates, to developers on Cloud readiness for their apps. Etc
Read more
Administrator in Banking
Enterprise(> 1000 emp.)
CAST Highlight for Application portfolio rationalization modernization cloudification
More features on cloudification, oss vulnerabilities identification. Decision making on Application portfolio rationalization, modernization, cloudification.
Read more
Madanmohan M.
Director center of excellence
Enterprise(> 1000 emp.)
Great Tool to assess your applications
It's easy to use and intuitive. I like that you can download a pdf to have the information of the code of the application that you are assessing.
Read more
Consultant in Capital Markets
Mid-Market(51-1000 emp.)
An Insightful and value-driven Software Intelligence solution, with large technology coverage
large technology coverage
very easy and quick to
setup
customization
options
vulnerabilities analysis (SCA features)
export of reports in editable
format

Internal Consultant in Information Technology and Services
Enterprise(>
1000 emp.)
Using CAST for enterprise application modernization
The facility to scan, analyze and present the results for the application
Read more
Javier Esteban C.
Solution Sales Specialist
Enterprise(> 1000 emp.)
Automated Assessment Solution is good
Agnostic Solution that fits all Cloud Migration
Read more
Udit A.
Solution Architect
Enterprise(> 1000 emp.)
CAST Highlight features are excellent and makes the product outcome as best in industry
Excellent design of UI looks and easy way to check all and portfolio insights. Based on the different features, the decision of product migration to cloud , improving code-quality in SDLC process makes easier job.
Read more
Lakshmi A.
Senior Member Technical
Enterprise(> 1000 emp.)
CAST Highlight is very user friendly and good for application scan and cloud migration analysis
Application Dashboard, Application Health, Cloud readiness, Roadblocks
Read more
Kalees T.
Technical Architect
Small-Business(50 or fewer emp.)
Aiming to migrate to Cloud or understanding your applications environment? Look for CAST Highlight
I have been through a few iterations of a cloud migration effort, and how I wish we had at our disposal a tool that could give us insights such as those offered by CAST Highlight.
Read more
Maamar F.
Director
Small-Business(50 or fewer emp.)
CAST Highlight gives a 360 view of an application
It assesses an application on Software Health, Elegance, and Agility and also indicates the cloud readiness percentage.
Read more
Bharat P.
Project Manager Cloud Solutions
Enterprise(> 1000 emp.)
CAST Highlight portfolio based on 2 business applications, CAST Highlight basic certification
Clear and compelling view on software elegance, views on Code Insights provide helpful and relevant software improvement candidates; Cloud Ready view on the application provide great recommendations based on local code scans.
Read more
Aleš .
Project Manager
Mid-Market(51-1000 emp.)